Innovative methods for detecting malware
July 17, 2020Creativity may not be the first word that pops into your head when thinking of cybersecurity, but as hackers develop innovative threats to systems, cybersecurity experts need to implement equally innovative and creative solutions in response.
Microsoft, in conjunction with Intel Labs, has come up with a new, creative approach to detecting malware that combines artificial intelligence, machine learning, and out-of-the-box thinking.
In a white paper shared in April 2020, the team at Microsoft and Intel introduced static malware-as-image network analysis (STAMINA).
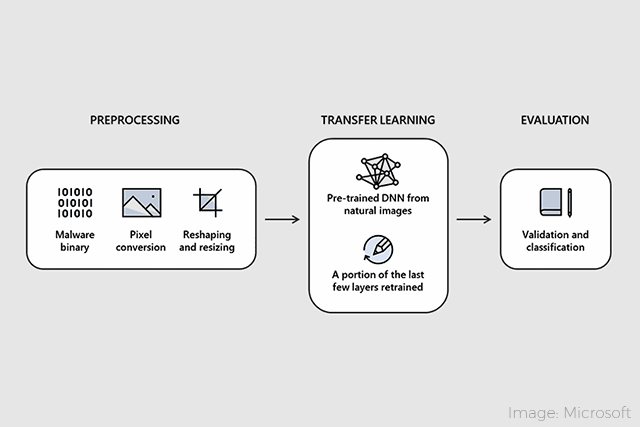
“In simple terms, the machine learning project starts out by taking binary files and converting them into two-dimensional images,” reports Paul Lilly in PCGamer. The images are created by transforming the bytes into a value between 0 and 255, correlating to pixel intensity. The width and height are then determined by file size, and the images are resized for ease of processing by the deep neural network (DNN).
Once the images are finalized, they are fed into a pre-trained DNN. The DNN uses a Microsoft data set of 2.2 million hashes (long strings of letters and numbers) of malware binaries that splits into segments, with 60% as known malware, 20% as validation, and 20% to test the effectiveness of the program.
“This second step is a process called transfer learning, which essentially helps the algorithm build upon its existing knowledge, while comparing images against its existing training,” says Lilly.
After the program has run, the results are reviewed to determine accuracy and effectiveness. Per the white paper, STAMINA accurately detects malware 99.07% of the time, with a 2.58% false positive rate.
Not only is STAMINA highly successful, it removes some of the downsides of current malware detection, which can include signature-matching inefficiencies, time consuming dynamic code analysis, and static analysis that can struggle to address code obfuscation.
Though STAMINA shows many benefits, there is one major drawback with the program in its current form: the larger the malware file the less effective STAMINA becomes.
This results from “software not being able to convert billions of pixels into JPEG images and then resizing,” states the white paper. Future work is planned for bigger data sets that provide more accuracy and for improvements to minimize power and performance impacts to the end-user.
Students at Capitol Tech studying cybersecurity are well prepared to develop innovative solutions to potential threats through courses such as secure data communications and cryptography, penetration testing, malware analysis/reverse engineering, and digital forensics and the Investigative Process.
Want to learn about cybersecurity? Capitol Tech offers bachelor’s, master’s and doctorate degrees in cyber and information security. Many courses are available both on campus and online. To learn more about Capitol Tech’s degree programs, contact admissions@captechu.edu.